Classify intrusion events into these categories as defined by the Cyber Kill Chain Model Implementing Cisco Cybersecurity Operations (210-255) The...
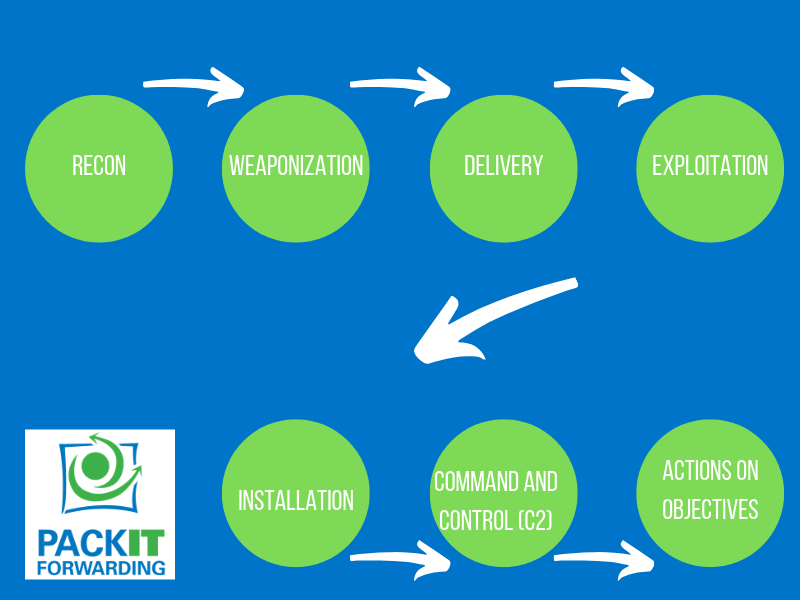

Classify intrusion events into these categories as defined by the Cyber Kill Chain Model Implementing Cisco Cybersecurity Operations (210-255) The...

Compare and contrast deterministic and probabilistic analysis Implementing Cisco Cybersecurity Operations (210-255) Deterministic Analysis Deterministic analysis uses data that is...

Identify a correlation rule to distinguish the most significant alert from a given set of events from multiple data sources...

Map DNS logs and HTTP logs together to find a threat actor Implementing Cisco Cybersecurity Operations (210-255) Map DNS, HTTP,...