Identify potentially compromised hosts within the network based on a threat analysis report containing malicious IP address or domains Implementing...
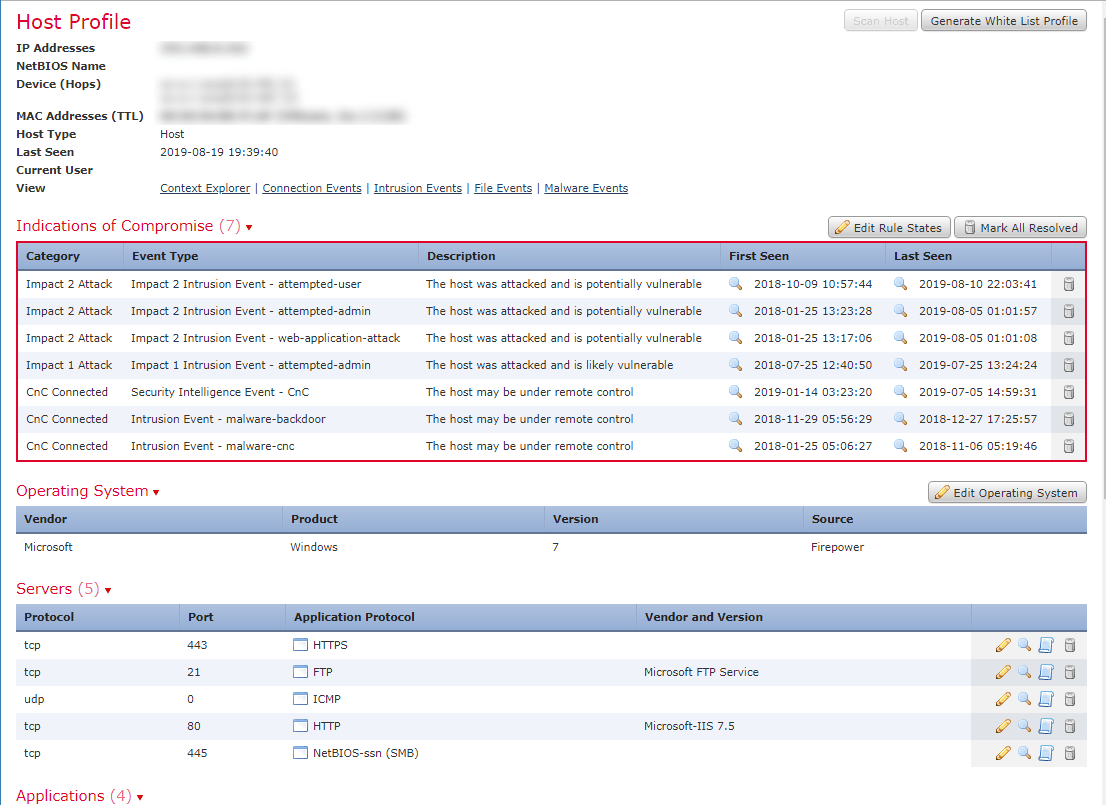

Identify potentially compromised hosts within the network based on a threat analysis report containing malicious IP address or domains Implementing...