Describe these concepts as they are documented in NIST SP800-86: evidence collection order, data integrity, data preservation, volatile data collection...


Describe these concepts as they are documented in NIST SP800-86: evidence collection order, data integrity, data preservation, volatile data collection...

Define these activities as they relate to incident handling Implementing Cisco Cybersecurity Operations (210-255) Identification Continuous monitoring of the environment...
Apply the NIST.SP800-61 r2 incident handling process to an event Implementing Cisco Cybersecurity Operations (210-255) The NIST.SP800-61 r2 incident handling...
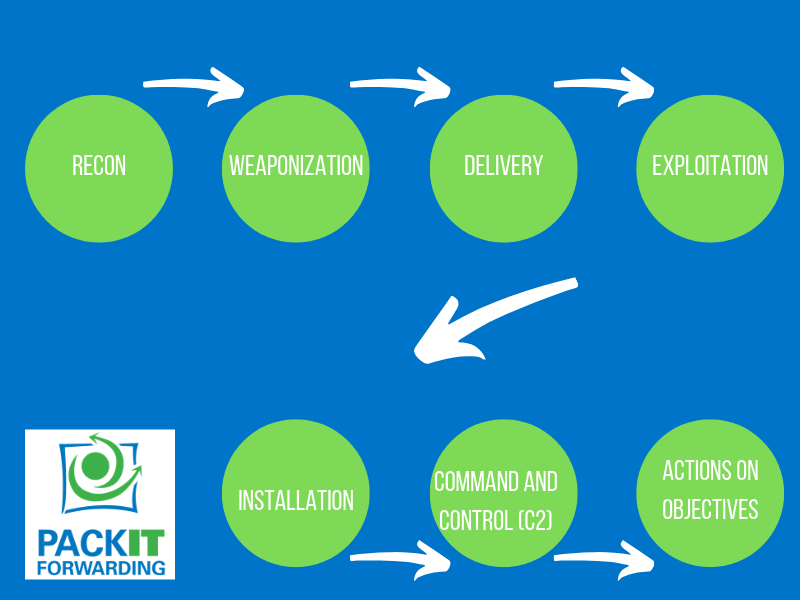
Classify intrusion events into these categories as defined by the Cyber Kill Chain Model Implementing Cisco Cybersecurity Operations (210-255) The...