Given a scenario, analyze the results of a network reconnaissance.
CompTIA Cybersecurity Analyst (CySA+) Certification Exam Objectives Version 3.0
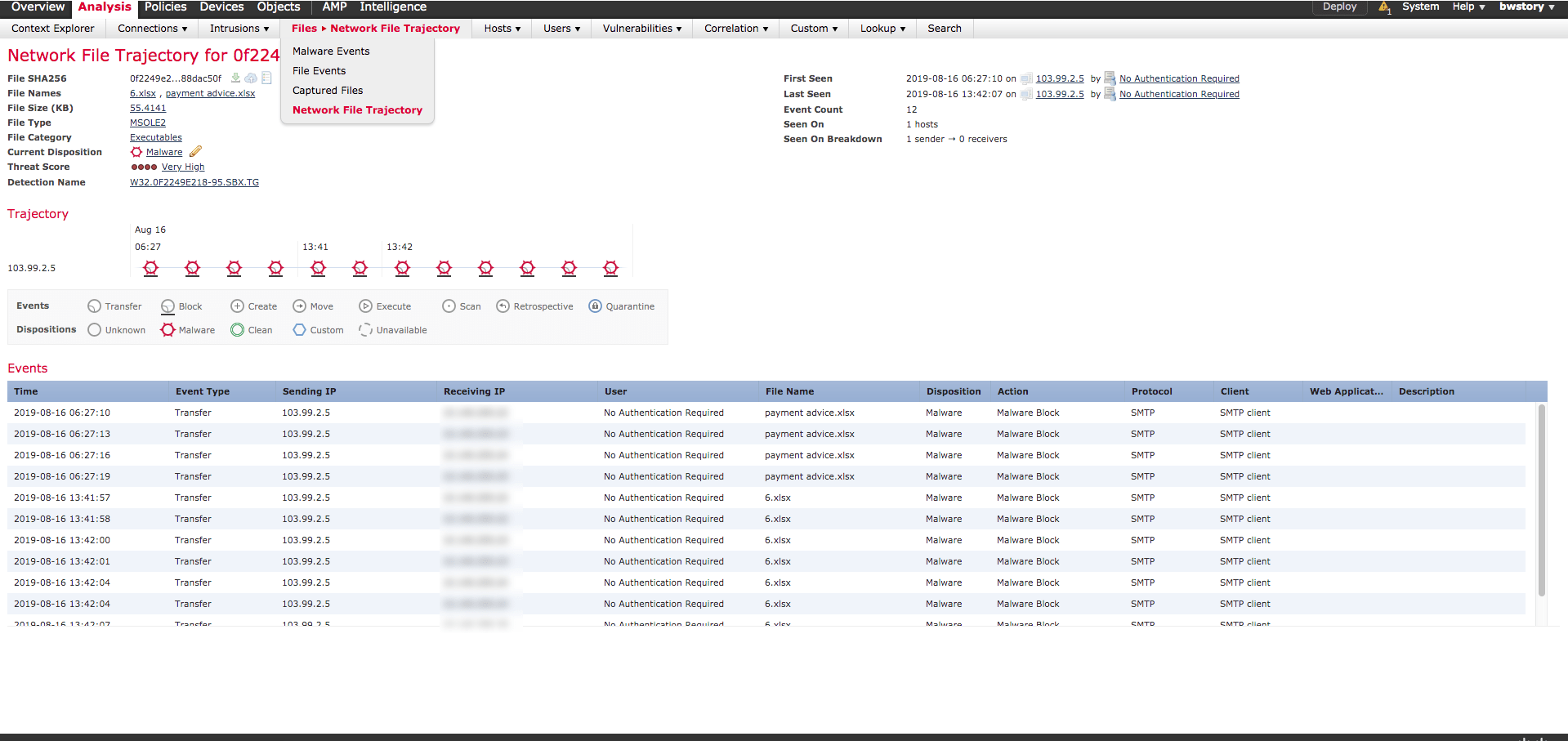
While gathering the reconnaissance about a network, the data must be turned into actionable information. The first type of analysis is the point in time analysis. Sources for such analysis may include packet captures, Netflow and wireless captures. Tools for analyzing these data sources may include packet analyzers like Wireshark, Netflow analyzers like
For longer periods of time, the data can be analyzed for baselines, trends, and patterns. The more you know about what is “normal” the easier it is to detect abnormalities. Security Information and Event Mangement (SIEM) tools such as qRadar and Splunk are one type of tool that can be useful in analyzing the data. MRTG, Solarwinds Orion, and LibreNMS are examples of tools that can use the Simple Network Management Protocol (SNMP) counters to present data for trending analysis.
Anomaly Analysis vs Trend Analysis
Anomaly analysis focuses on finding unusual or abnormal events. These anomalies could include abnormal traffic volume, abnormal traffic types or a system with higher than normal traffic profile. One issue with anomaly analysis is that many systems tend to create false positives that must be investigated. Anomaly analysis focuses on