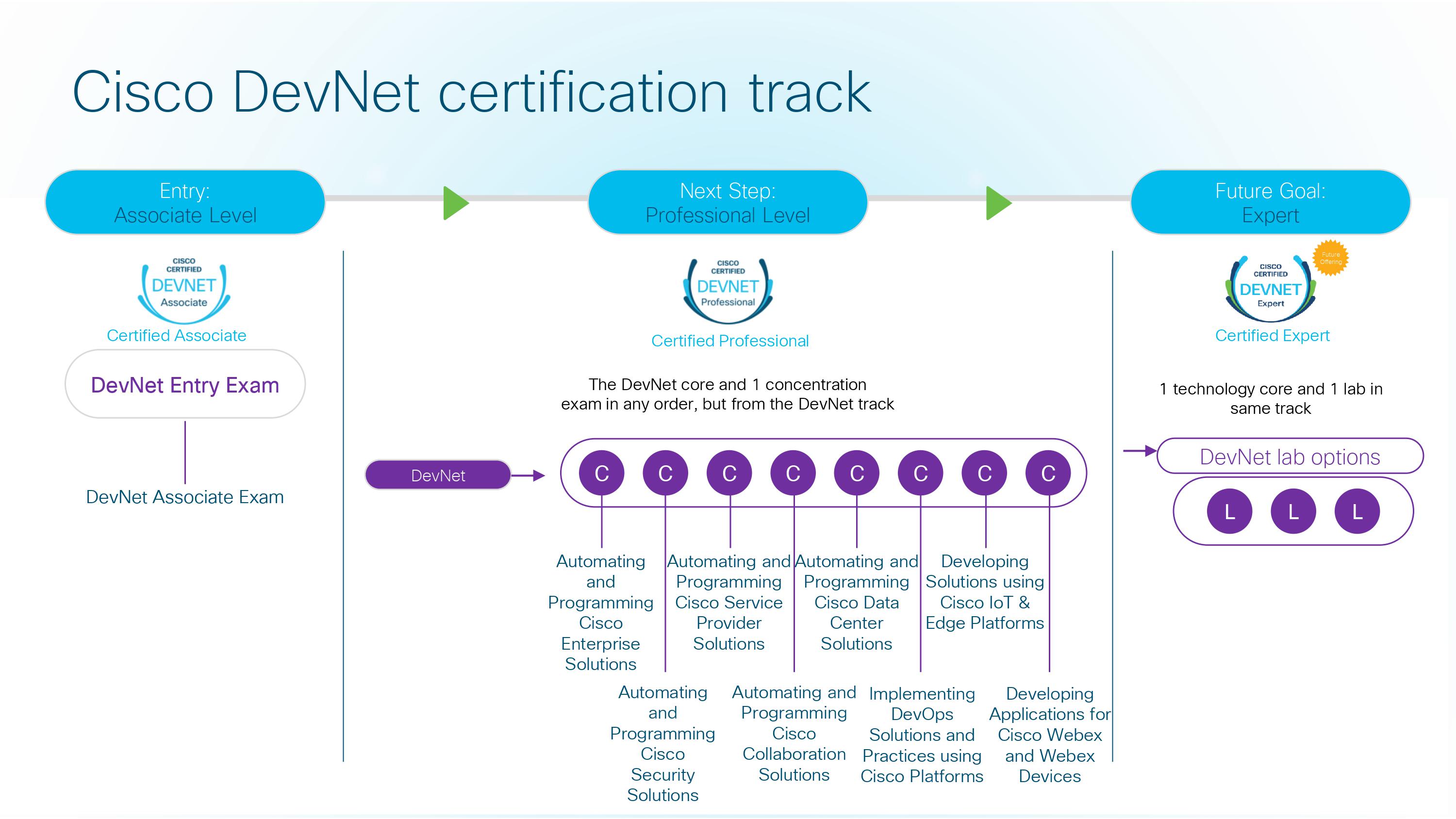
Given a scenario, analyze common symptoms to select the best course of action to support incident response.
CompTIA Cybersecurity Analyst (CySA+) Certification Exam Objectives Version 3.0
Common Network-Related Symptoms
- Bandwidth consumption: It is important to have a baseline before an incident to know what is normal on the network. Deviation from the baseline can be an indication of a security incident.
- Beaconing: Traffic from infected systems that could include DNS probes or command and control connections.
- Irregular peer-to-peer communication: Most traffic in today’s enterprise computing environment is
client to server traffic. Traffic that deviates from this pattern may be an indication of a security incident. - Rogue devices on the network: Enterprises often have a standard for devices purchased so a “rogue” device may be easy to spot by mac address or other interrogation methods.
- Scan sweeps: Pings or other scans can indicate that a bad actor is scanning the network for hosts to attack.
- Unusual traffic spikes: Increases in the amount of traffic, even low bandwidth, but high connections, can indicate an issue.
Common Host-Related Symptoms
- Processor consumption: A host with high CPU usage that is not normal can be a sign of compromise.
- Memory consumption: A host with high memory usage that is not normal can be a sign of compromise.
- Drive capacity consumption: A host with storage being used more than normal can be a sign of compromise.
- Unauthorized software: Software that is not authorized in the environment could be a sign of compromise.
- Malicious processes: Processes may show up in the process list that
are known bad. - Unauthorized changes: If a stringent change control process is in place and an unauthorized change is detected, it could signal a security incident.
- Unauthorized privileges: Changes to account permissions can signal an incident.
- Data exfiltration: The theft of data from a device. Any data missing or deleted could be a sign. There are also tools to track the movement of data to the outside (Data Loss Prevention [DLP]).
Common Application-Related Symptoms
- Anomalous Activity: an application behaving in a way that is not normal could be a sign of a security incident.
- Introduction of New Accounts: new accounts within an application’s authentication database could be a sign of a security incident.
- Unexpected Output: Strange output in an application could be a sign that the application has been altered.
- Unexpected Outbound Communication: Unexpected communication to outside hosts should be investigated.
- Service Interruption: When an application is no longer able to service requests, it may be an indication of an attack.
- Memory Overflows: When an application overflows
it’s memory allocation it can indicate a buffer overflow attack.