Identify stages in the cyberattack lifecycle and firewall mitigations that can prevent attacks.
Palo Alto PCNSA Study Guide v10

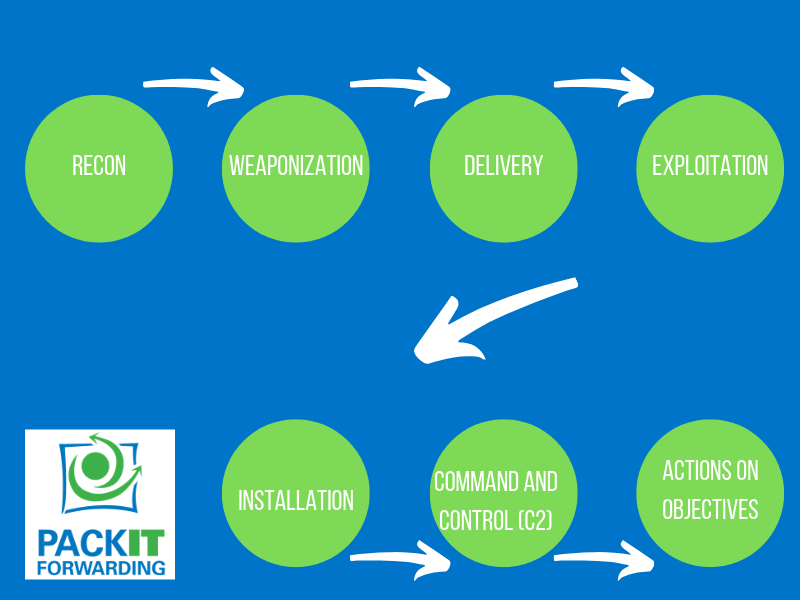
The cyberattack lifecycle, or cyber kill chain, is a model to show the stages of an attack and how it can be prevented. If any one stage is stopped, the entire attack is stopped. Generally the earlier in the chain, the easier it is to stop.
Reconnaissance
This stage is when the attacker gains information about the target. Information can come from open source intelligence like Twitter, LinkedIn and the corporate website. Attackers will also scan publicly facing services for vulnerabilities.
Prevention:
- Traffic inspection to detect and prevent port scans and host sweeps.
- Implement security awareness training to limit information of a sensitive nature from being posted publically.
Weaponization
Weaponization is the process where the attacker determines how to deliver malicious payloads to take advantage of weaknesses that were found.
Prevention:
- Because this takes place outside of the organization, there is no prevention of this step.
Delivery
This phase is when the payload is delivered into the victim organization. This could be via files, e-mail messages or malicious websites.
Prevention:
- Gain visibility into all traffic, even encrypted traffic
- Block high-risk applications
- Extend protections outside of the perimeter to remote and mobile devices.
- Protect against perimeter breaches using URL filtering to block malicious or risky websites
- Block known bad traffic, malware and C2 using IPS, anti-malware, DNS monitoring, sinkholing and file/content blocking.
- Detect unknown malware to stop Day-0
- Provide user education about potential attacks such as phishing, watering hole attacks, email links, and other attacks
Exploitation
This is the stage where the attacker deploys an exploit against a vulnerability to gain entry to the organization.
Prevention:
- Patch systems continuously
- User education against phishing
- Block vulnerability exploits on endpoints
- Deliver new protections automatically
Installation
After the attackers have gotten access to the network, they will install additional tools to maintain access, persistence and escalate their privileges.
Prevention:
- Prevent malware installation on endpoints, networks and cloud servers
- Establish security zones that provide monitoring and inspection of all traffic (Zero Trust)
- Limit local administrator access
- User education on recognizing malware infection
Command and Control (C2)
With malware installed, the attackers can control the system. They will establish a channel for control and for sending data back to them.
Prevention:
- Block outbound C2 communication (beaconing)
- Block file uploads that match patterns like Social Security Numbers
- Redirect malicious C2 to internal sinkholes
- Block outbound communication to known bad URLs
- Create a database of malicious domains for prevention through DNS monitoring
- Limit the attacker’s ability to move laterally. Zero Trust
Actions on the Objective
The actions completed by the attacker to achieve their goal. This could be data exfiltration, destruction, defacing a website, or to extort the victim organization.
Prevention:
- Threat hunting using threat intelligence tools
- Monitor and inspect all interzone traffic
- Enforce user access between secure zones
- Block outbound C2 traffic
- Block outbound malicious URL traffic
- Implement granular controls on applications and user file transfers
- Eliminate known archiving and transfers
- Limit lateral movement.