Identify these key elements in an intrusion from a given PCAP file : Source address, Destination address, Source port, Destination port, Protocols, and Payloads
Implementing Cisco Cybersecurity Operations (210-255)
PCAP files are a way of storing packet data captured using a packet sniffer like Wireshark. The Wireshark website has dozens of example packet captures that can help you get familiar with various protocols. For this objective I am using a simple HTTP packet capture from their repository. It is an older capture and was saved with a .CAP extension, but changing it to .PCAP will allow it to be opened in modern versions of Wireshark.
First, let’s look at the Ethernet II frame. As you can see below, Wireshark has parsed the packet to show us the source and destination MAC addresses.

Next, let’s take a look at the IPv4 packet that is encapsulated by the Ethernet II frame above. Again Wireshark has dissected the headers for us. We can easily see the source and destination IP Addresses, the DSCP value, and protocol among other useful bits of information.

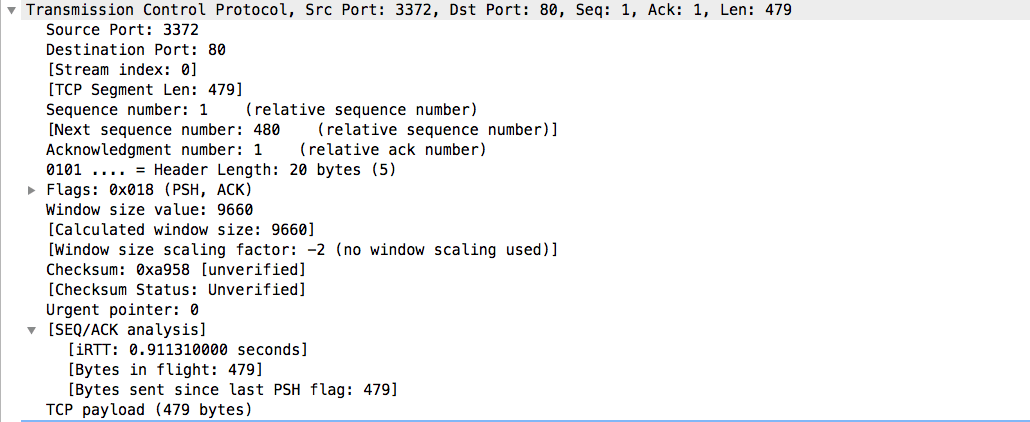
At layer 4 of the OSI model, we get to the transport layer and that is the next part of the packet capture. In this case, it is a TCP datagram. The Wireshark dissection shows us the source and destination ports, the sequence number, the length of the datagram, and other analysis. Note that the next sequence number is determined by adding the length to the current sequence number. If this doesn’t match, you may have some malicious actor altering packets to accomplish an attack. Also, note the TCP flags are listed. This is important when tracking the TCP Three-Way handshake.

Finally, we will skip up to the Application layer to look at the actual HTTP protocol that is being sent across the network. First, notice the request method, in this case, GET. The next two important bits of information is the URI and the Host that will tell you what is being accessed. The User-Agent is also a very important bit of information for cybersecurity analysts. Although it can be changed by many programs, it can help fingerprint what type of software is making the request.

