Describe the retrospective analysis method to find a malicious file, provided file analysis report Implementing Cisco Cybersecurity Operations (210-255) The...
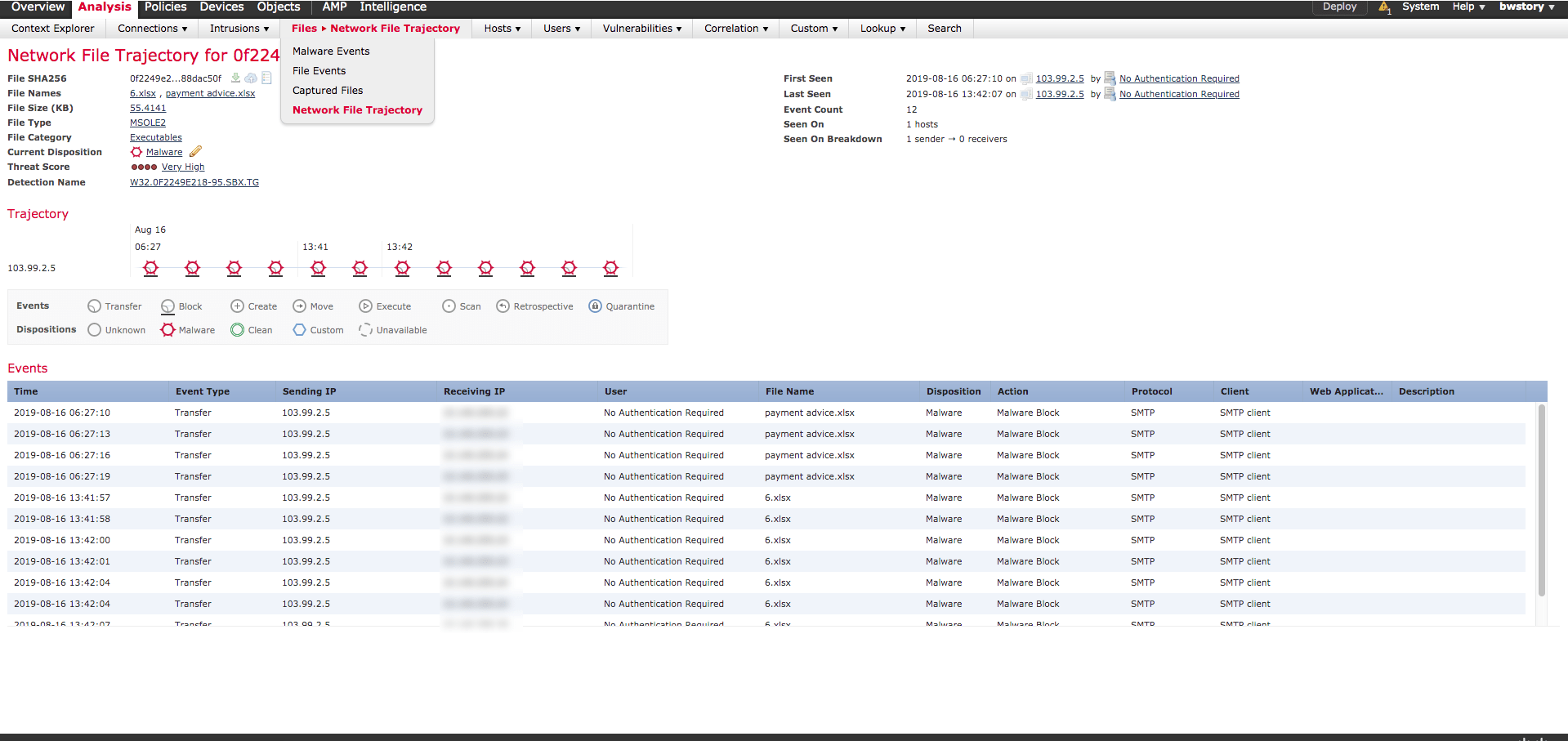

Describe the retrospective analysis method to find a malicious file, provided file analysis report Implementing Cisco Cybersecurity Operations (210-255) The...

Describe 5-tuple correlation Implementing Cisco Cybersecurity Operations (210-255) Describe the 5-tuple approach to isolate a compromised host in a grouped...

Interpret common data values into a universal format Implementing Cisco Cybersecurity Operations (210-255) For this objective, I would suggest using...

Describe the process of data normalization Implementing Cisco Cybersecurity Operations (210-255) Data normalization is the process of removing duplicate information...