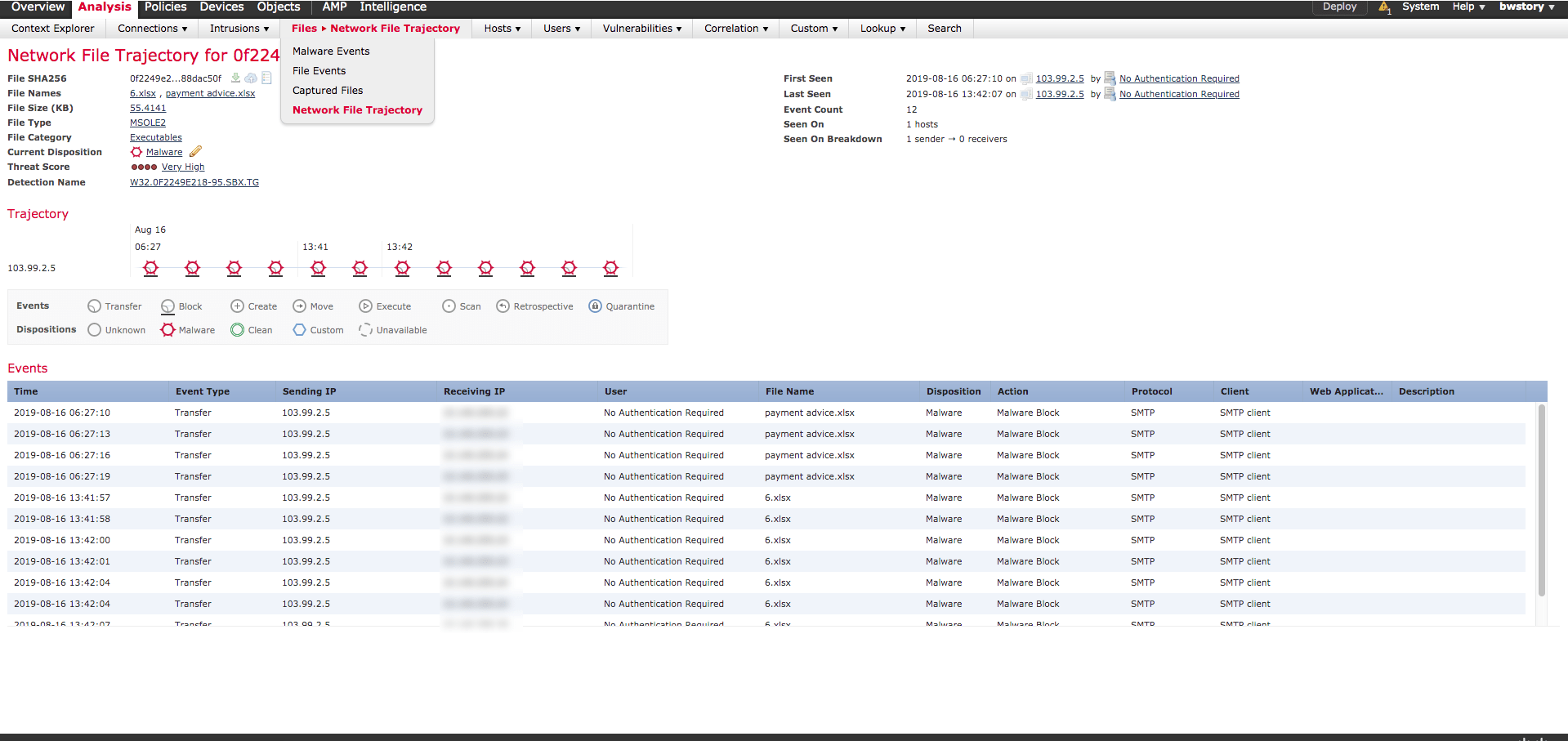
Describe the retrospective analysis method to find a malicious file, provided file analysis report
Implementing Cisco Cybersecurity Operations (210-255)

The above image is a screenshot from a Cisco Firepower Management Center. In particular, it is a Network File Trajectory. In this case, it’s not overly interesting since the file was only seen going from one Internet host to one internal host. In a more complex scenario, FMC would be coupled with AMP for Endpoints. This would allow an analyst to see how a file has traversed from host to host as the infection was spread.
You can also see when a new file was originally marked clean or unknown and later marked as malicious. This type of event is known as a retrospective event.