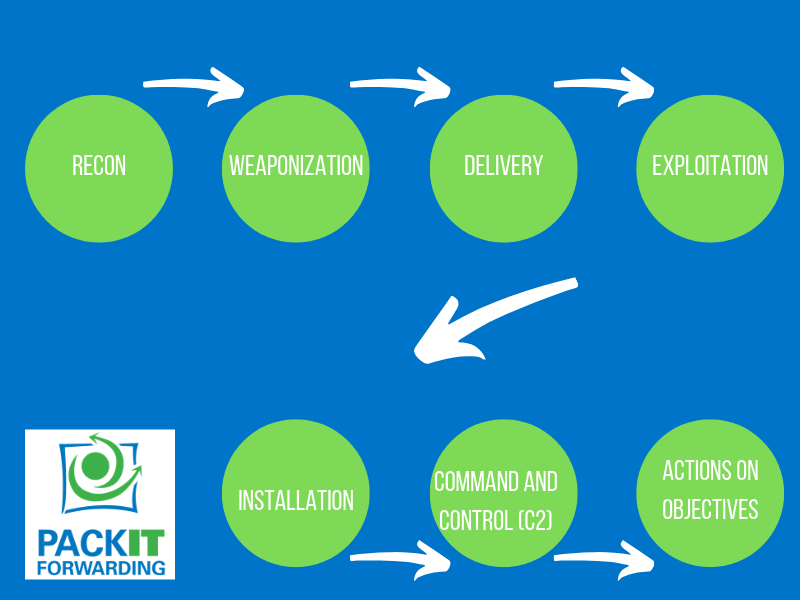
Classify intrusion events into these categories as defined by the Cyber Kill Chain Model
Implementing Cisco Cybersecurity Operations (210-255)
The cyber kill chain model outlines all of the steps necessary for a cyber attack to be successful. If the chain is broken, the attack will fail. The cyber kill chain is also an ordered list so remembering it in order is important. MalwareJake’s blog offers a mnemonic to remember the chain in order. “Real women date engineers in commando armor.”
Real women date engineers in commando armor.
http://malwarejake.blogspot.com/2016/11/kill-chain-mnemonic.html
Reconnaissance
The reconnaissance phase of the cyber kill chain consists of the attacker gathering information about their target. Activities during this phase do not require the attacker to gain any non-public access to the target network or resources. Some places that an attacker will get information about the target include Social Networks, Google and the target’s public website.
Weaponization
Weaponization involves taking an exploit and turning it into something usable. An example would be embedding code in a word document to exploit a vulnerability when attached to an e-mail or other delivery means.
Delivery
Delivery of the attack can take many forms. It could be a direct network connection, a payload in an e-mail, a phishing website or many other vectors.
Exploitation
Exploitation is when the code is executed to exploit a vulnerability in the hardware or software being targeted.
Installation
Installation is when the attacker establishes persistence inside the attacked organization. The goal is to survive reboots and to avoid detection by anti-malware and anti-virus software.
Command and Control (C2)
C2 traffic is how the installed software phones home via various methods to get instructions from the attackers. This traffic is also known as beaconing and can be very low volume to avoid detection.
Action on Objectives
This is the final phase of the attack. This is when the attacker is able to affect one or more of the CIA triad.

1 thought on “CCNA CyberOps SECOPS – Objective 5.1”