Interpret common artifact elements from an event to identify an alert Implementing Cisco Cybersecurity Operations (210-255) IP Address (source/destination) IP...


Interpret common artifact elements from an event to identify an alert Implementing Cisco Cybersecurity Operations (210-255) IP Address (source/destination) IP...
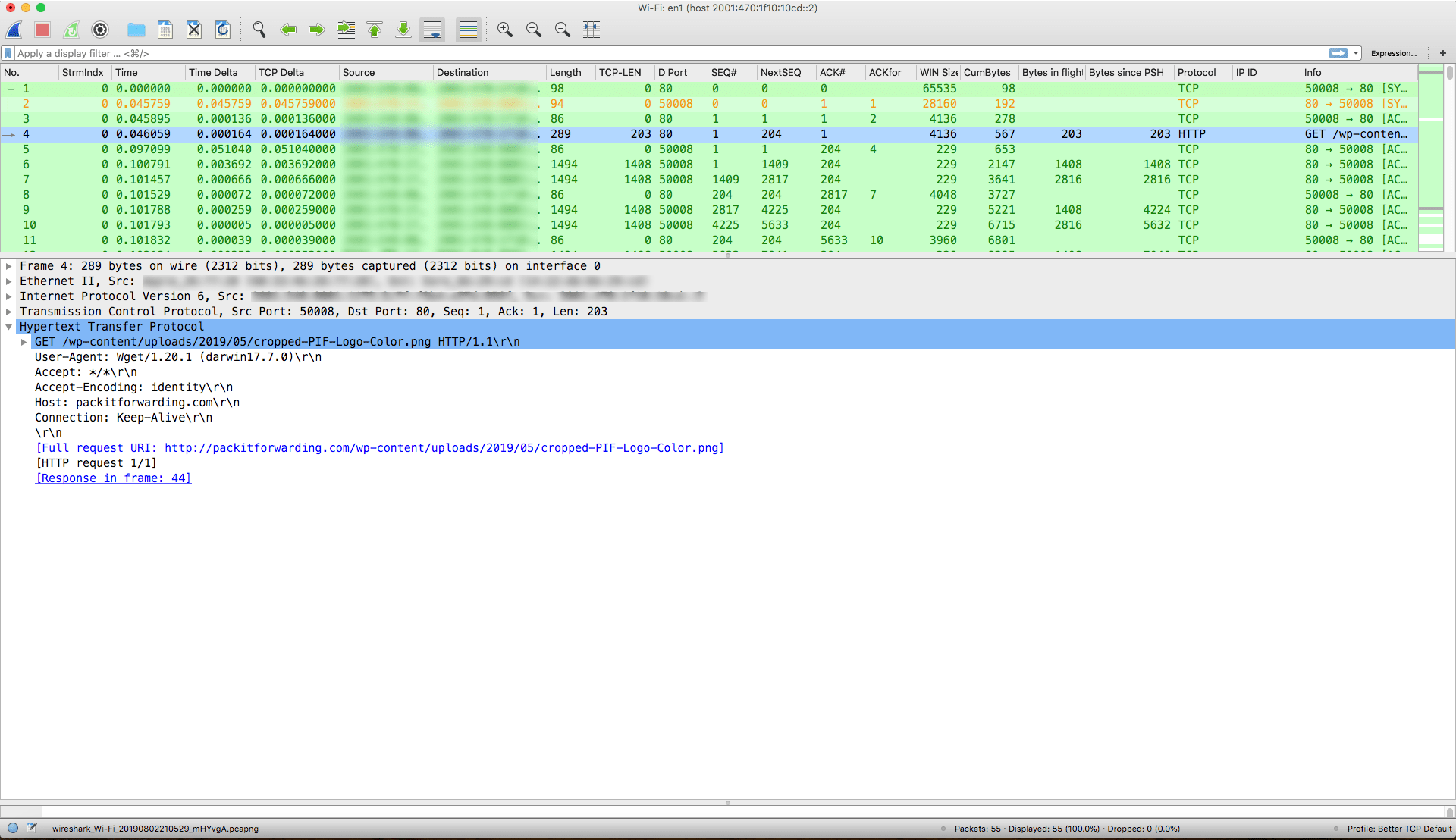
Extract files from a TCP stream when given a PCAP file and Wireshark Implementing Cisco Cybersecurity Operations (210-255) For this...
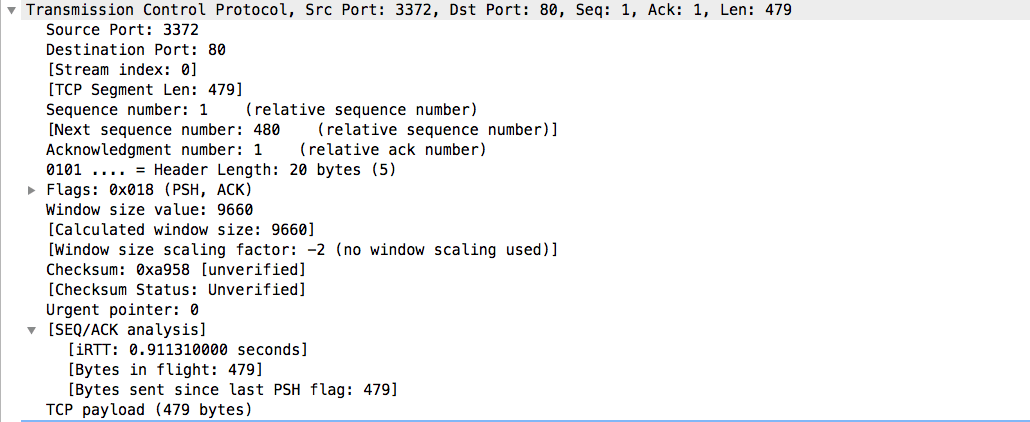
Identify these key elements in an intrusion from a given PCAP file : Source address, Destination address, Source port, Destination...

Identify the elements from a NetFlow v5 record from a security event Implementing Cisco Cybersecurity Operations (210-255) When it comes...