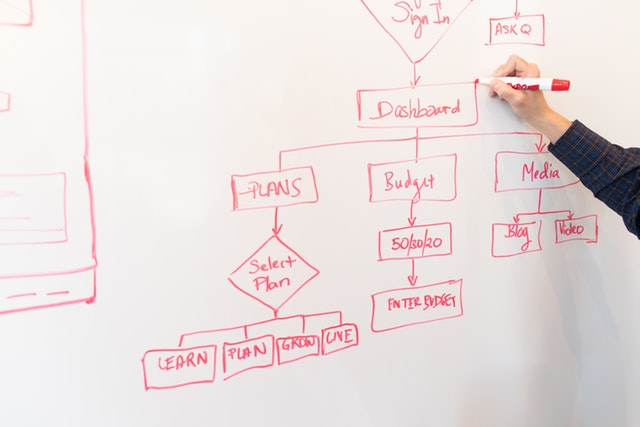
Apply the NIST.SP800-61 r2 incident handling process to an event
Implementing Cisco Cybersecurity Operations (210-255)
The NIST.SP800-61 r2 incident handling process document contains several example scenarios. These are all contained in Appendix A of the document. Below are some of the suggested questions for each phase from section A-1 of the document.
Preparation:
Would the organization consider this activity to be an incident? If so, which of the organization’s policies does this activity violate? (Section 2.1)
NIST.SP800-61 r2 Appendix A Section 1
What measures are in place to attempt to prevent this type of incident from occurring or to limit its impact? (Section 3.1.2)
Detection and Analysis:
What precursors of the incident, if any, might the organization detect? Would any precursors cause the organization to take action before the incident occurred? (Sections 3.2.2, 3.2.3)
What indicators of the incident might the organization detect? Which indicators would cause someone to think that an incident might have occurred? (Sections 3.2.2, 3.2.3)
What additional tools might be needed to detect this particular incident? (Section 3.2.3)
How would the incident response team analyze and validate this incident? What personnel would be involved in the analysis and validation process? (Section 3.2.4)
To which people and groups within the organization would the team report the incident? (Section 3.2.7)
How would the team prioritize the handling of this incident? (Section 3.2.6)
Containment, Eradication, and Recovery:
What strategy should the organization take to contain the incident? Why is this strategy preferable to others? (Section 3.3.1)
What could happen if the incident were not contained? (Section 3.3.1)
What additional tools might be needed to respond to this particular incident? (Sections 3.3.1, 3.3.4)
Which personnel would be involved in the containment, eradication, and/or recovery processes? (Sections 3.3.1, 3.3.4)
What sources of evidence, if any, should the organization acquire? How would the evidence be acquired? Where would it be stored? How long should it be retained? (Sections 3.2.5, 3.3.2, 3.4.3)
Post-Incident Activity:
Who would attend the lessons learned meeting regarding this incident? (Section 3.4.1)
What could be done to prevent similar incidents from occurring in the future? (Section 3.1.2)
What could be done to improve detection of similar incidents? (Section 3.1.2)
General Questions:
How many incident response team members would participate in handling this incident? (Section 2.4.3)
Besides the incident response team, what groups within the organization would be involved in handling this incident? (Section 2.4.4)
To which external parties would the team report the incident? When would each report occur? How would each report be made? What information would you report or not report, and why? (Section 2.3.2)
What other communications with external parties may occur? (Section 2.3.2)
What tools and resources would the team use in handling this incident? (Section 3.1.1)
What aspects of the handling would have been different if the incident had occurred at a different day and time (on-hours versus off-hours)? (Section 2.4.2)
What aspects of the handling would have been different if the incident had occurred at a different physical location (onsite versus offsite)? (Section 2.4.2)