Identify potentially compromised hosts within the network based on a threat analysis report containing malicious IP address or domains Implementing...
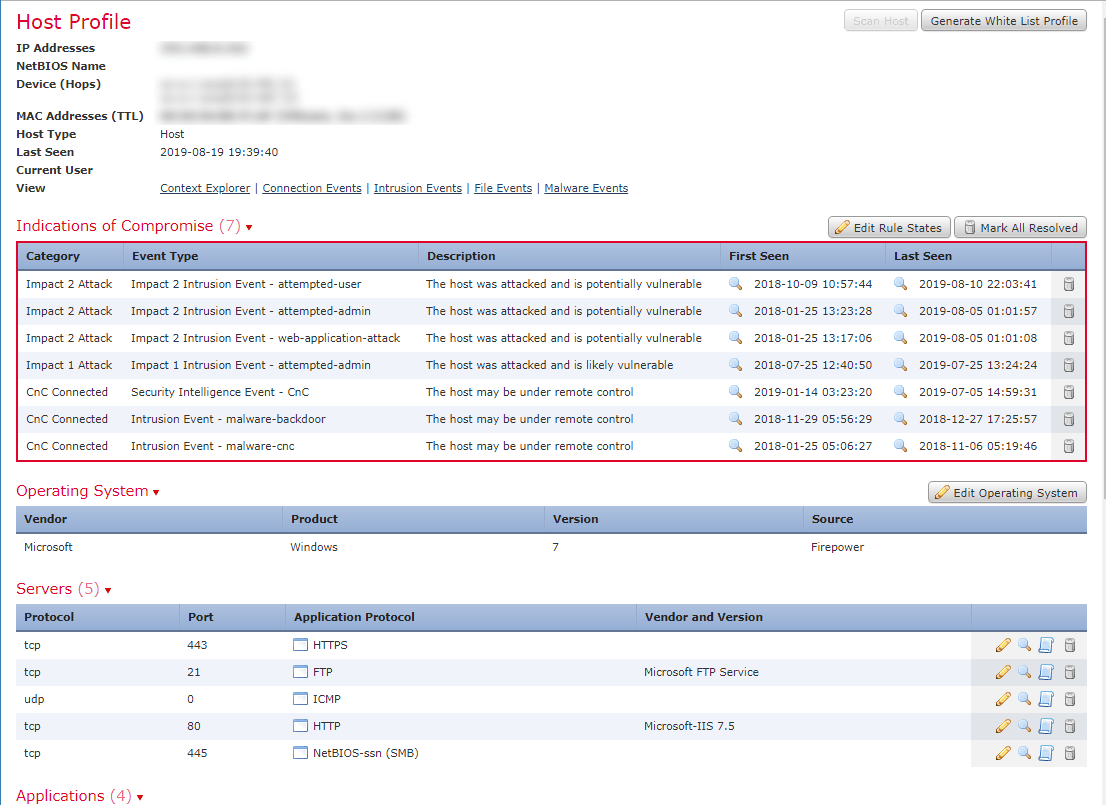

Identify potentially compromised hosts within the network based on a threat analysis report containing malicious IP address or domains Implementing...

Rackstuds are one of those things that you didn’t know you needed until you first get some. Cage nuts have...
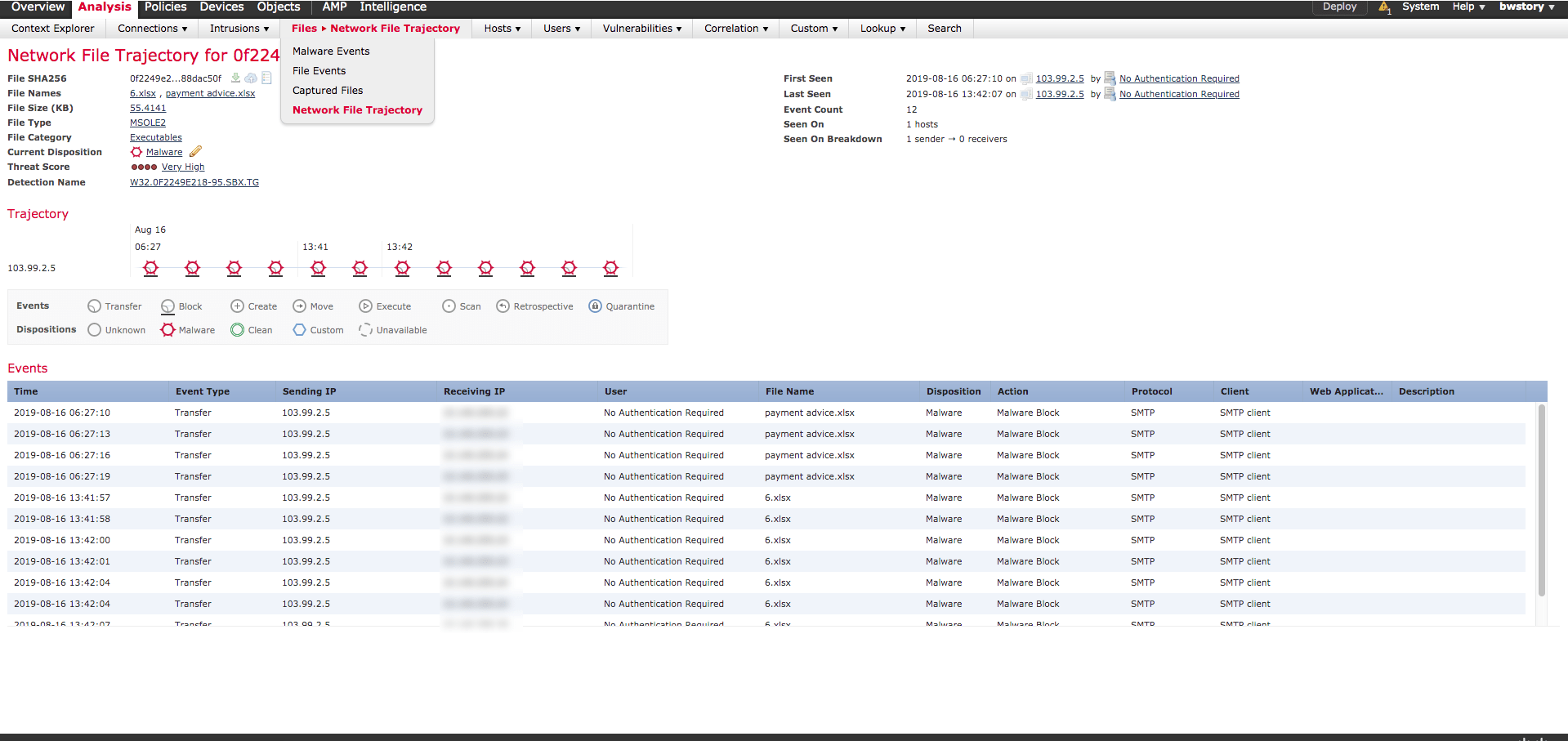
Describe the retrospective analysis method to find a malicious file, provided file analysis report Implementing Cisco Cybersecurity Operations (210-255) The...

Describe 5-tuple correlation Implementing Cisco Cybersecurity Operations (210-255) Describe the 5-tuple approach to isolate a compromised host in a grouped...